某天,在鼓捣一个ems系统,想用来做成新闻资讯类网站。弄了好多天,各个框架和结构都差不多了,重新调整了结构,一个偶然的机会,发现搜索框点击的时候不能自动清空先前的内容,于是想添加一段js代码去修改,找了半天,没有看到一个类似main.js的网站通用js代码,倒是发现一个奇怪的js文件,并且是加密的,这肯定引起了我的兴趣哈。看看这段代码。
var _0xe2a1=["\x63\x6C\x61\x73\x73\x4E\x61\x6D\x65","\x61\x63\x74\x69\x76\x65","\x69\x64","\x70\x61\x72\x65\x6E\x74\x4E\x6F\x64\x65","\x6C\x69","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x73\x42\x79\x54\x61\x67\x4E\x61\x6D\x65","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x6C\x65\x6E\x67\x74\x68","\x64\x69\x73\x70\x6C\x61\x79","\x73\x74\x79\x6C\x65","\x43","\x62\x6C\x6F\x63\x6B","\x6E\x6F\x72\x6D\x61\x6C","\x6E\x6F\x6E\x65","\x68\x65\x69\x67\x68\x74","\x73\x63\x72\x6F\x6C\x6C\x54\x6F\x70","\x73\x68\x6F\x77","\x23\x67\x6F\x74\x6F\x70","\x68\x69\x64\x65","\x63\x6C\x69\x63\x6B","\x63\x6F\x64\x65\x5F\x68\x6F\x76\x65\x72","\x61\x74\x74\x72","\x23\x63\x6F\x64\x65\x5F\x69\x6D\x67","\x63\x6F\x64\x65","\x68\x6F\x76\x65\x72","\x23\x63\x6F\x64\x65","\x72\x65\x61\x64\x79","\x73\x63\x72\x6F\x6C\x6C","\x64\x6F\x6D\x61\x69\x6E","\x68\x6F\x68\x75\x61\x6E\x2E\x63\x6F\x6D","\x69\x6E\x64\x65\x78\x4F\x66","\x31\x32\x37\x2E\x30\x2E\x30\x2E\x31","\x6C\x6F\x63\x61\x6C\x68\x6F\x73\x74","\u8BE5\u6A21\u677F\u5C1A\u672A\u6388\u6743\u6B64\u7AD9\u4F7F\u7528\x2C\u8BF7\u8D2D\u4E70\u6388\u6743","\x68\x72\x65\x66","\x68\x74\x74\x70\x3A\x2F\x2F\x77\x77\x77\x2E\x78\x69\x75\x7A\x68\x61\x6E\x77\x61\x6E\x67\x2E\x63\x6F\x6D"];function ThinkOver(_0x31c5x2,_0x31c5x3){if(_0x31c5x2[_0xe2a1[0]]==_0xe2a1[1]){return ;} ;var _0x31c5x4=_0x31c5x2[_0xe2a1[3]][_0xe2a1[2]];var _0x31c5x5=document[_0xe2a1[6]](_0x31c5x4)[_0xe2a1[5]](_0xe2a1[4]);for(i=0;i<_0x31c5x5[_0xe2a1[7]];i++){if(i==_0x31c5x3){_0x31c5x2[_0xe2a1[0]]=_0xe2a1[1];document[_0xe2a1[6]](_0x31c5x4+_0xe2a1[10]+i)[_0xe2a1[9]][_0xe2a1[8]]=_0xe2a1[11];} else {_0x31c5x5[i][_0xe2a1[0]]=_0xe2a1[12];document[_0xe2a1[6]](_0x31c5x4+_0xe2a1[10]+i)[_0xe2a1[9]][_0xe2a1[8]]=_0xe2a1[13];} ;} ;} ;function b(){h=$(window)[_0xe2a1[14]]();t=$(document)[_0xe2a1[15]]();if(t>h){$(_0xe2a1[17])[_0xe2a1[16]]();} else {$(_0xe2a1[17])[_0xe2a1[18]]();} ;} ;$(document)[_0xe2a1[26]](function (_0x31c5x7){b();$(_0xe2a1[17])[_0xe2a1[19]](function (){$(document)[_0xe2a1[15]](0);} );$(_0xe2a1[25])[_0xe2a1[24]](function (){$(this)[_0xe2a1[21]](_0xe2a1[2],_0xe2a1[20]);$(_0xe2a1[22])[_0xe2a1[16]]();} ,function (){$(this)[_0xe2a1[21]](_0xe2a1[2],_0xe2a1[23]);$(_0xe2a1[22])[_0xe2a1[18]]();} );} );$(window)[_0xe2a1[27]](function (_0x31c5x7){b();} );
一个js代码的解密并不难,难得是搞明白这些乱七八糟的是什么加密,难的是对那些进行了代码混淆使得可读性极差的代码的整理与翻译!
很明显,上面这个代码进行了混淆!0xe2a1这类变量名搞得像蓝屏代码错误号,吓死人,一般人没认真看还真搞不明白这是些什么东西。
首先我们搜索“_0xe2a1”,可以发现存在46个这种变量。
我们将其命名为strone,全部替换之。_0x31c5x2,_0x31c5x3,_0x31c5x4,_0x31c5x5,_0x31c5x6,_0x31c5x7全是这些变量,可以跟随个人喜欢,换成喜欢的变量名。下面的就是混淆,使得不容易阅读代码。
_0xe2a1的值才是加密的重点。有经验的程序员应当一眼就可以看出,这是我标题里面所说的Javascript \x 16进制加密。这个解密非常简单,网上方法很多,直接用document.write就可以写出明文。代码如下。
var _0xc828=["\x63\x6C\x61\x73\x73\x4E\x61\x6D\x65","\x61\x63\x74\x69\x76\x65","\x69\x64","\x70\x61\x72\x65\x6E\x74\x4E\x6F\x64\x65","\x6C\x69","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x73\x42\x79\x54\x61\x67\x4E\x61\x6D\x65","\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64","\x6C\x65\x6E\x67\x74\x68","\x64\x69\x73\x70\x6C\x61\x79","\x73\x74\x79\x6C\x65","\x43","\x62\x6C\x6F\x63\x6B","\x6E\x6F\x72\x6D\x61\x6C","\x6E\x6F\x6E\x65","\x68\x65\x69\x67\x68\x74","\x73\x63\x72\x6F\x6C\x6C\x54\x6F\x70","\x73\x68\x6F\x77","\x23\x67\x6F\x74\x6F\x70","\x68\x69\x64\x65","\x63\x6C\x69\x63\x6B","\x63\x6F\x64\x65\x5F\x68\x6F\x76\x65\x72","\x61\x74\x74\x72","\x23\x63\x6F\x64\x65\x5F\x69\x6D\x67","\x63\x6F\x64\x65","\x68\x6F\x76\x65\x72","\x23\x63\x6F\x64\x65","\x72\x65\x61\x64\x79","\x73\x63\x72\x6F\x6C\x6C","\x64\x6F\x6D\x61\x69\x6E","\x68\x6F\x68\x75\x61\x6E\x2E\x63\x6F\x6D","\x69\x6E\x64\x65\x78\x4F\x66","\x31\x32\x37\x2E\x30\x2E\x30\x2E\x31","\x6C\x6F\x63\x61\x6C\x68\x6F\x73\x74","\u8BE5\u6A21\u677F\u5C1A\u672A\u6388\u6743\u6B64\u7AD9\u4F7F\u7528\x2C\u8BF7\u8D2D\u4E70\u6388\u6743","\x68\x72\x65\x66","\x68\x74\x74\x70\x3A\x2F\x2F\x77\x77\x77\x2E\x78\x69\x75\x7A\x68\x61\x6E\x77\x61\x6E\x67\x2E\x63\x6F\x6D"];
for(i=0;i<_0xc828.length;i++){
document.write(i+"="+_0xc828[i]+"");
}
把上面的代码放在html的<script></script>之间运行就可以解密了,解密结果如下
0=className1=active2=id3=parentNode4=li5=getElementsByTagName6=getElementById7=length8=display9=style10=C11=block12=normal13=none14=height15=scrollTop16=show17=#gotop18=hide19=click20=code_hover21=attr22=#code_img23=code24=hover25=#code26=ready27=scroll28=domain29=hohuan.com30=indexOf31=127.0.0.132=localhost33=该模板尚未授权此站使用,请购买授权34=href
作为解密来说,http://tool.lu/js的功能非常强大。将所有的代码放到对话框,即可解密全文。
解密后明码如下
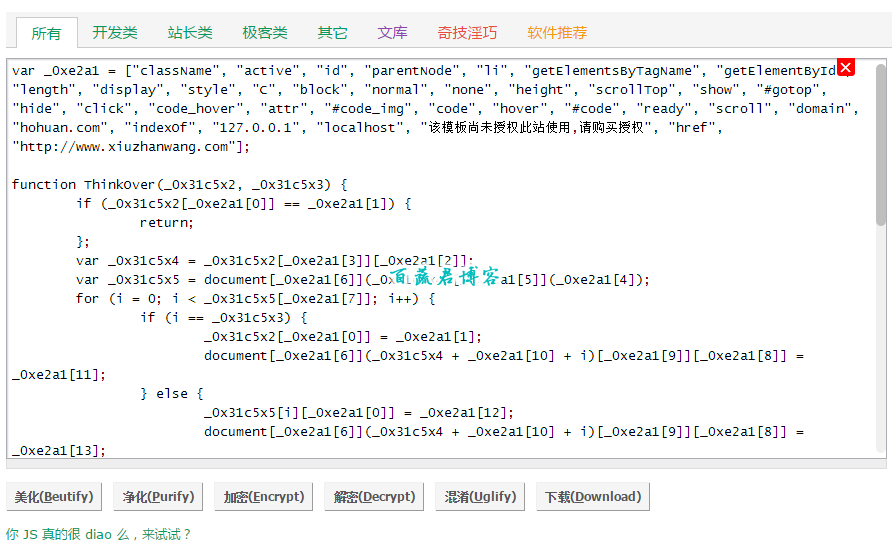
var _0xe2a1 = ["className", "active", "id", "parentNode", "li", "getElementsByTagName", "getElementById", "length", "display", "style", "C", "block", "normal", "none", "height", "scrollTop", "show", "#gotop", "hide", "click", "code_hover", "attr", "#code_img", "code", "hover", "#code", "ready", "scroll", "domain", "maiseed.com", "indexOf", "127.0.0.1", "localhost", "买种子就上百蔬网", "href", "http://www.maiseed.com"];
function ThinkOver(_0x31c5x2, _0x31c5x3) {
if (_0x31c5x2[_0xe2a1[0]] == _0xe2a1[1]) {
return;
};
var _0x31c5x4 = _0x31c5x2[_0xe2a1[3]][_0xe2a1[2]];
var _0x31c5x5 = document[_0xe2a1[6]](_0x31c5x4)[_0xe2a1[5]](_0xe2a1[4]);
for (i = 0; i < _0x31c5x5[_0xe2a1[7]]; i++) { if (i == _0x31c5x3) { _0x31c5x2[_0xe2a1[0]] = _0xe2a1[1]; document[_0xe2a1[6]](_0x31c5x4 + _0xe2a1[10] + i)[_0xe2a1[9]][_0xe2a1[8]] = _0xe2a1[11]; } else { _0x31c5x5[i][_0xe2a1[0]] = _0xe2a1[12]; document[_0xe2a1[6]](_0x31c5x4 + _0xe2a1[10] + i)[_0xe2a1[9]][_0xe2a1[8]] = _0xe2a1[13]; }; }; }; function b() { h = $(window)[_0xe2a1[14]](); t = $(document)[_0xe2a1[15]](); if (t > h) {
$(_0xe2a1[17])[_0xe2a1[16]]();
} else {
$(_0xe2a1[17])[_0xe2a1[18]]();
};
};
$(document)[_0xe2a1[26]](function(_0x31c5x7) {
b();
$(_0xe2a1[17])[_0xe2a1[19]](function() {
$(document)[_0xe2a1[15]](0);
});
$(_0xe2a1[25])[_0xe2a1[24]](function() {
$(this)[_0xe2a1[21]](_0xe2a1[2], _0xe2a1[20]);
$(_0xe2a1[22])[_0xe2a1[16]]();
}, function() {
$(this)[_0xe2a1[21]](_0xe2a1[2], _0xe2a1[23]);
$(_0xe2a1[22])[_0xe2a1[18]]();
});
});
$(window)[_0xe2a1[27]](function(_0x31c5x7) {
b();
});
这个解密和上面的html解密一样。”你js真的很diaome?来试试,大气哦”,不同的是他将那些原来链接到一起,堆砌成一句话的js代码进行了结构整理,使得结构清晰,很容易看懂,但是如果使用您自己的代码混淆,你也看不出来吧?
可以看到解密出来的结果中有网址和提示,因为他涉及到一些网站需要的js切换代码,所以不能完全删除这个js文件,如果我们把这些内容替换成我们自己的内容,再加密放回去,会不会很爽?
就像前面说的,搞明白了是什么加密,就可以进行加密与反加密。
仔细查看_0xe2a1变量,会发现他是由很多双引号括起来的多个值的一个字串,熟悉的知道这是\x 16进制加密,他的加解密代码如下
是否启用\x加密
在线的可以到魔酷阁http://www.mokuge.com/tool/js_x16/或者周超博客http://www.zc520.cc/js/62.html这里来进行加解密。
这段代码猛看上去大部分都是\x 16进制加密,其实在里面明显还有一段代码他是不同的。
\u8BE5\u6A21\u677F\u5C1A\u672A\u6388\u6743\u6B64\u7AD9\u4F7F\u7528\x2C\u8BF7\u8D2D\u4E70\u6388\u6743
这个是unicode对中文的加密,在线的可以在魔酷阁http://www.mokuge.com/tool/native2ascii/ 或者站长助手http://tool.chinaz.com/tools/unicode.aspx
换成自己想要的东东,替换回去,就可以弄成我们想要的效果了。